
Phishing is a malicious try to collect delicate data comparable to usernames, passwords, and bank card particulars by disguising as a reliable entity by digital communication. With the arrival of Synthetic Intelligence (AI), phishing assaults have change into extra refined, making them tougher to identify. Nevertheless, there are nonetheless methods to establish and keep away from falling prey to those AI-generated phishing emails. Let’s discover ten easy methods.
Introduction to Phishing and AI-generated Emails
Phishing has been a menace to web customers for years. Historically, cybercriminals manually created phishing emails, however at present, they use AI to generate persuasive and customized messages. These AI programs can craft emails that mimic the fashion and tone of professional corporations, tricking even essentially the most vigilant customers. Understanding the character of those threats is step one in defending your self.
Understanding the Fundamentals of AI-generated Content material
AI-generated content material is created by algorithms that be taught from huge quantities of information on the web. These algorithms can analyze how real emails are written and replicate that fashion in phishing emails. Regardless of their sophistication, AI-generated emails typically include refined flaws that may give them away. Understanding what to search for is essential.
Manner 1: Analyze the Sender’s E-mail Handle
One of many best methods to identify a phishing electronic mail is to take a look at the sender’s tackle. Phishers might use an electronic mail that appears much like a professional one however with slight variations. For instance, an electronic mail from “[email protected]” as an alternative of “[email protected]” ought to increase a crimson flag. At all times double-check the sender’s electronic mail tackle earlier than taking any motion.
Right here is another instance of phishing mail I acquired from the next electronic mail id:
[email protected]
Once you obtain this sort of electronic mail from [email protected] or from others, there are a number of crimson flags to contemplate:
- Complicated E-mail Prefix: The lengthy and convoluted prefix shouldn’t be typical for official firm emails.
- Model Identify Utilization: The usage of “Meta” could possibly be an try to falsely affiliate the e-mail with the well-known firm, Meta Platforms Inc.
- Generic E-mail Area: Official firm emails often come from their very own area, not from frequent electronic mail companies like Outlook.
- Worry Techniques: Phrases like “restriction” and “case” could be used to scare you into taking motion.
- Random Characters: The “d25” appears arbitrary and could possibly be an try to make the e-mail look distinctive or official.
Briefly, this electronic mail has a number of hallmarks of a phishing try. It’s greatest to keep away from interacting with it—don’t click on on any hyperlinks, obtain attachments, or reply with private data. If doubtful, contact the corporate it purports to characterize by verified means. At all times err on the aspect of warning with sudden emails.
Under is the screenshot of the e-mail content material:
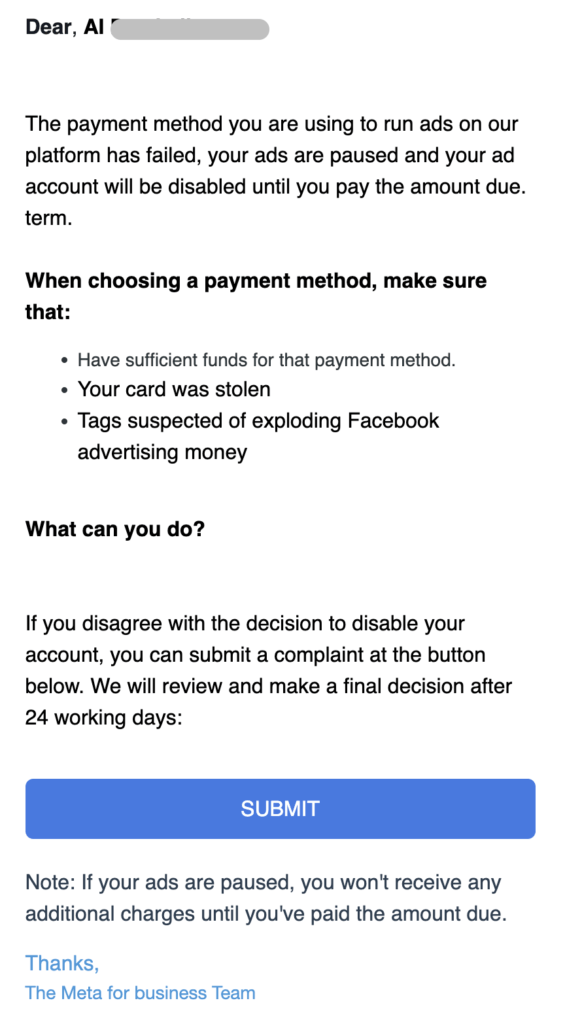

As you evaluate the screenshot, search for the everyday indicators of phishing that we mentioned. Pay shut consideration to the language used, any requests for private data, or prompts to click on on hyperlinks or obtain information. Keep in mind, professional organizations won’t ask for delicate data through electronic mail. If something within the electronic mail raises suspicion, it’s best to keep away from any interplay with the message and report it as phishing to your electronic mail supplier. At all times confirm the authenticity of any sudden or suspicious communication by contacting the official supply immediately by their verified channels.
Manner 2: Search for Generic Greetings and Signal-offs
AI-generated phishing emails typically use generic greetings like “Expensive Buyer” or “Expensive Consumer.” Official corporations often personalize their emails together with your title. Equally, the sign-offs in phishing emails could be impersonal or lack the same old contact data you’d count on from an actual firm. If the e-mail doesn’t tackle you immediately or ends abruptly, be cautious.
Manner 3: Test for Spelling and Grammar Errors
Although AI has change into fairly superior, it might nonetheless make errors {that a} human wouldn’t. Search for odd phrasings, misspelled phrases, or grammar points. Whereas everybody makes typos from time to time, skilled communications from respected organizations sometimes undergo a number of rounds of enhancing and needs to be freed from such errors.
Manner 4: Discover the Tone and Fashion Inconsistencies
The tone and magnificence of an AI-generated electronic mail would possibly really feel off. Should you obtain an electronic mail from an entity you’re aware of, evaluate it to earlier communications. Does it sound prefer it was written by the identical individual? Is the fashion per what you’ve seen earlier than? If one thing feels misplaced, belief your instincts.
Manner 5: Be Cautious of Pressing or Threatening Language
Phishers typically use pressing or threatening language to create a way of panic and immediate hasty actions. Phrases like “speedy motion required” or “your account will likely be suspended” are frequent ways. Official corporations perceive the significance of buyer relations and are unlikely to make such calls for through electronic mail.
Manner 6: Scrutinize Embedded Hyperlinks and Attachments
AI-generated phishing emails might include hyperlinks or attachments that result in malicious web sites or include malware. Hover over any hyperlinks with out clicking to see the precise URL. If it seems to be suspicious or doesn’t match the context of the e-mail, don’t click on it. Be equally cautious with attachments; they need to solely be opened in case you are anticipating them and are certain of the supply.
Manner 7: Take into account the Plausibility of the E-mail’s Request
Typically, phishing emails make requests that appear uncommon or implausible. If an electronic mail asks you for delicate data like passwords or financial institution particulars, it’s a crimson flag. Official organizations have safe processes for dealing with delicate data and won’t ask you to supply it through electronic mail.
Manner 8: Use Superior E-mail Safety Instruments
Many electronic mail companies now provide built-in security measures that may assist establish phishing emails. These instruments analyze incoming messages for recognized phishing signatures and provide you with a warning if one thing seems to be suspicious. Be certain these options are enabled and maintain them up to date.
Manner 9: Maintain Up to date on the Newest Phishing Methods
Cybercriminals are always evolving their ways, so staying knowledgeable concerning the newest phishing schemes is essential. There are a lot of sources on-line the place you possibly can find out about new phishing tendencies. By staying knowledgeable, you could be looking out for brand spanking new methods and methods.
Manner 10: Educate Your self and Others About Phishing Methods
Information is energy. Educate your self, your loved ones, buddies, and colleagues concerning the risks of phishing and the way to acknowledge phishing makes an attempt. Sharing information is among the greatest defenses towards these cyber threats.
Conclusion and Proactive Steps Ahead
Phishing is a critical and evolving menace, particularly with the involvement of AI in producing convincing pretend emails. By being vigilant and taking proactive steps, you possibly can considerably scale back your threat of falling sufferer to phishing assaults. At all times keep skeptical of sudden emails, confirm the sources, and when doubtful, contact the corporate immediately utilizing a trusted methodology. Do not forget that the mix of know-how and consciousness is the most effective defend towards these cyber threats. Maintain your wits about you, and keep secure on-line.